Although the IT profession covers a wide range of job descriptions and responsibilities, certain challenges facing IT professionals are universal. The challenge is always about how to stay up-to-date with new developments while taking care of the day-to-day.
Insights: IT Security
Corporations are constantly threatened by information security breaches. Learn how to effectively execute a comprehensive information security strategy.
CommandHound has worked with clients in a variety of industries who deal with sensitive information on a daily basis.
The worldwide cyberattacks in the news lately have worried businesses and individuals alike.
The ransomware attacks Petya and WannaCry have affected commercial businesses, governmental entities, and individuals by the thousands. But while the media focuses on these external attacks, internal network security threats remain one of the most common problems in security management.
In the wake of the UK Parliament’s recent network security attack, it’s clear that no matter how well-designed our IT security systems and internal controls are, there’s always a risk of your organization falling victim to a cyber threat.
Headache-causing. Frustrating. Sluggish. These are some of the terms that go through our heads when trying to decode the complex regulatory requirements of Sarbanes-Oxley (SOX).
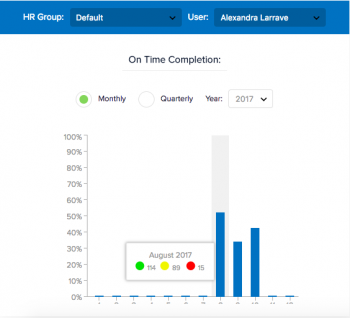
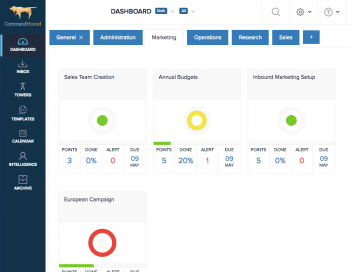
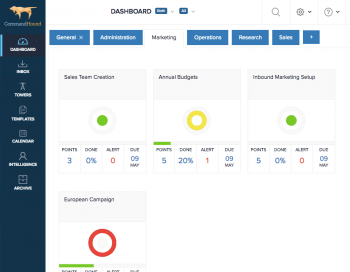
Why do some of your employees get all tasks done on time and as expected, but others can’t seem to have the same success rate, even when those tasks are critical and are designed to avoid, transfer, or reduce risks to the business?
Is it their motivation? Their DNA? Is it compensation? Is it culture?
What are the biggest challenges faced by companies when implementing the COBIT 5 framework into their organization? We gathered information from multiple sources to find the top three.
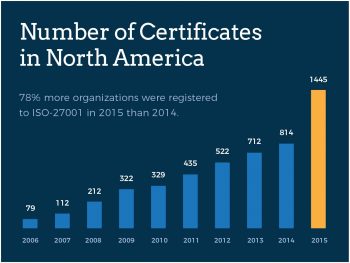
We dived deep into how companies set up Information Security Management Systems (ISMS) and found 8 key trends that lead to a successful ISO-27001 certification.