Headache-causing. Frustrating. Sluggish. These are some of the terms that go through our heads when trying to decode the complex regulatory requirements of Sarbanes-Oxley (SOX).
Insights: IT Security
It looks like the European Union’s new GDPR will go into effect on May 25, 2018. Companies that fail to comply with its rules and regulations will face fines of up to $20 million euros (or 4% of sales for the preceding year). This is definitely not a trivial update.
Cyber security seems like a very complex issue that requires deep, and seldom available, expertise to do it right. Here is a quick checklist that our information security users have turned into a Template in CommandHound for others to use. This checklist goes after the low hanging fruit by applying the 80/20 rule.
The worldwide cyberattacks in the news lately have worried businesses and individuals alike.
The ransomware attacks Petya and WannaCry have affected commercial businesses, governmental entities, and individuals by the thousands. But while the media focuses on these external attacks, internal network security threats remain one of the most common problems in security management.
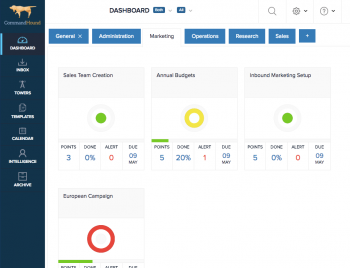
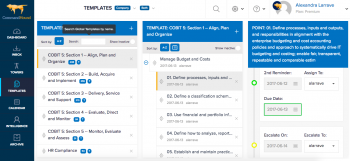
Have you tried to implement a comprehensive information security framework like ISO 27001 or COBIT but nobody is doing what they are supposed to do? A lack of accountability in the workplace is often the main reason.
After the Enron and Worldcom scandals of 2001, the Sarbanes-Oxley Act (SOX) was enacted by Congress to help prevent certain types of fraudulent practices. Among other things, SOX has had critical implications for IT. Not only because of the role information technology plays in all businesses nowadays but because of SOX’s industry-leading Section 802 data retention requirements.
It looks like the European Union’s new GDPR will go into effect on May 25, 2018. Companies that fail to comply with its rules and regulations will face fines of up to $20 million euros (or 4% of sales for the preceding year). This is definitely not a trivial update.
Cyber security seems like a very complex issue that requires deep, and seldom available, expertise to do it right. Here is a quick checklist that our information security users have turned into a Template in CommandHound for others to use. This checklist goes after the low hanging fruit by applying the 80/20 rule.
Have you tried to implement a comprehensive information security framework like ISO 27001 or COBIT but nobody is doing what they are supposed to do? A lack of accountability in the workplace is often the main reason.
Deciding to implement a comprehensive information security framework like ISO 27001 or COBIT is not a trivial thing. These frameworks are comprehensive, cross-functional, broad reaching, and culture-changing. Here are 3 compliance software tools to help you through the process.